-
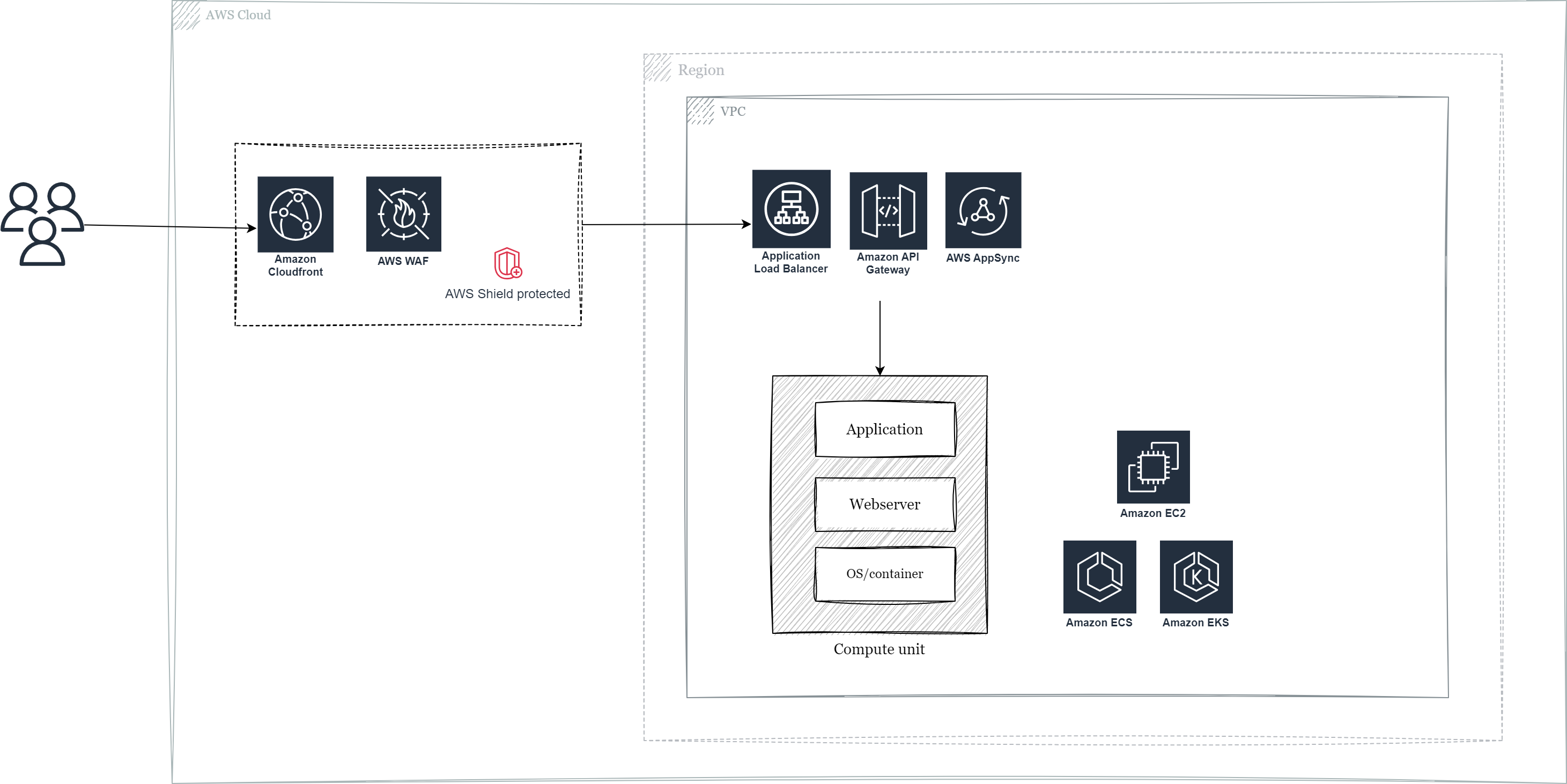
Protect your webapps from malicious traffic with AWS Web Application Firewall
According to DataDogs State of Cloud Security Report, a substantial portion of cloud workloads are excessively privileged and many virtual machines remain publicly exposed to the internet. In this post I will explain how AWS Web Application Firewall can protect your webapps.
-
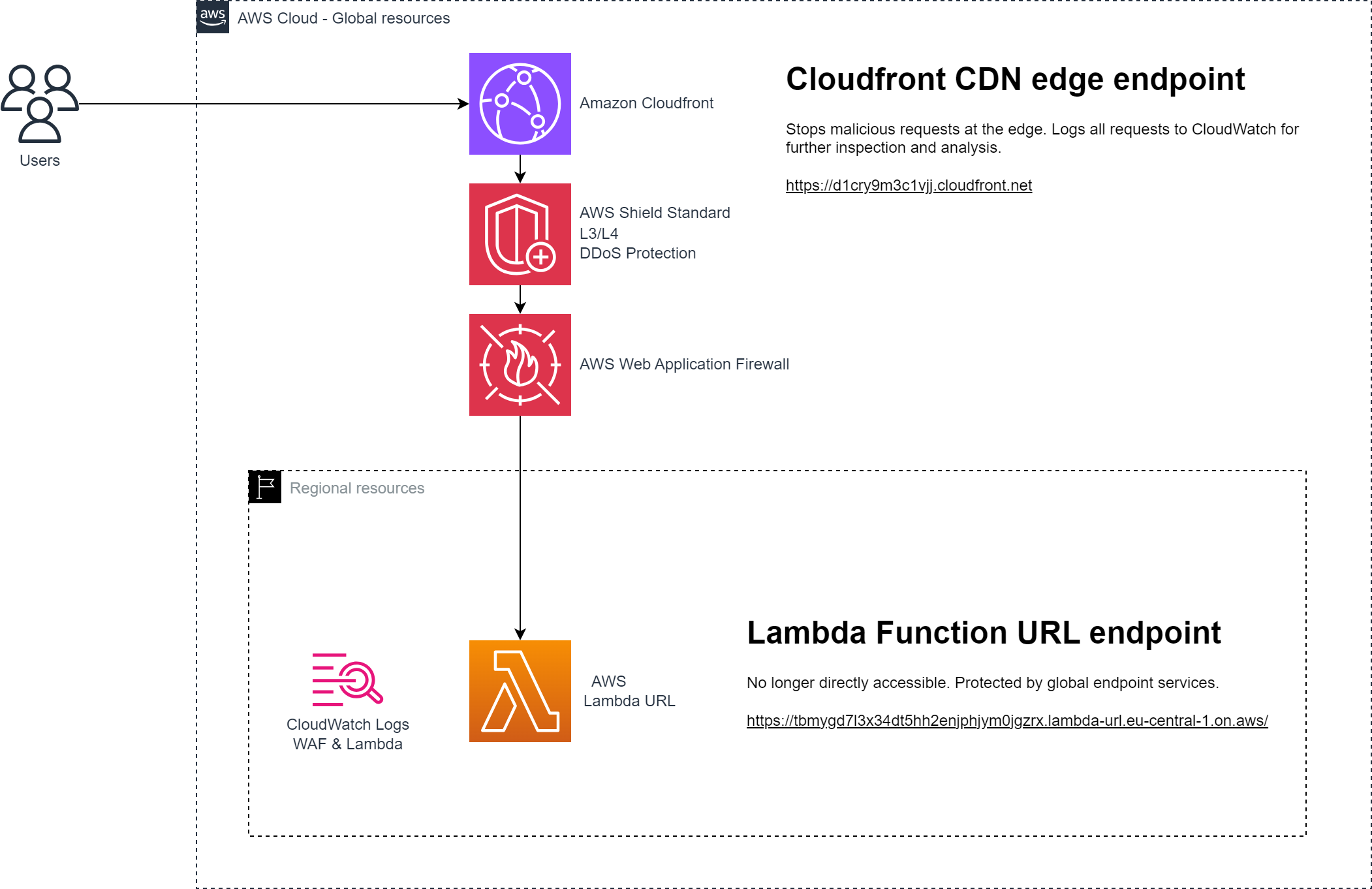
Develop lightweight and secure REST APIs with AWS Lambda Function URL and Terraform
This post demonstrates how to leverage AWS Lambda Function URL for lightweight REST APIS, and how to configure Cloudfront and WAF for protection, all done with Terraform.
-
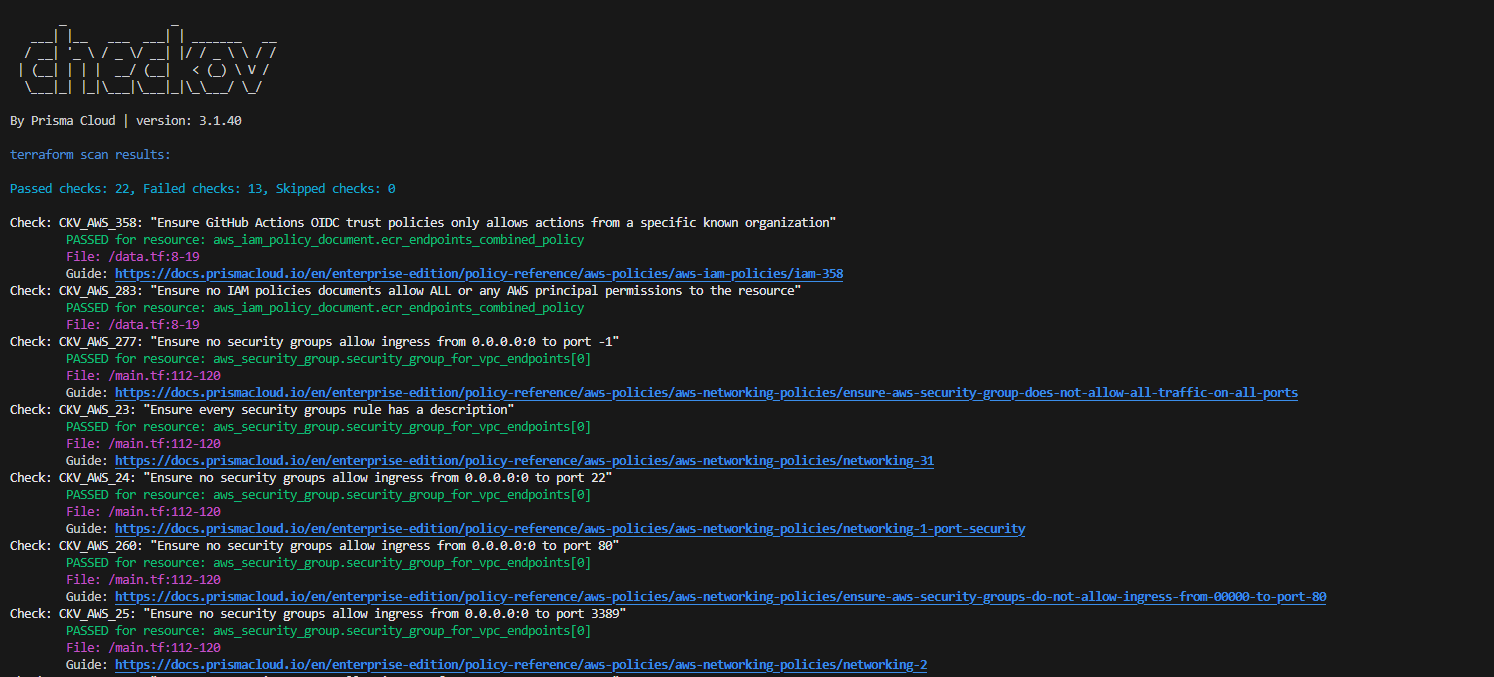
Move fast and avoid surprises – Shift-left on cloud security with Policy-as-Code
Security issues can be fatal. Compromises can lead to sensitive information getting into the hands of malicious actors. For companies, it could lead to substantial damage to trust and reputation. In the series “Move fast and avoid surprises” I’m elaborating on topics and concepts I’ve learned that have had major impact in real-life situations. In the…
-

Move fast and avoid surprises – Be Well-Architected
In the series “Move fast and avoid surprises” I’m elaborating on topics and concepts I’ve learned that have had major impact in real-life situations. In the modern software industry, being fast is not sufficient on it’s own, if you get caught up in problems by breaking things along the way. I rather prefer to avoid surprises. To be able to make…
-

AWS re:Invent guide – My approach for a successful experience
The AWS re:Invent learning conference is the highlight of the year for many cloud professionals. But how can you make sure to avoid disappointments and get the most of out the experience? Read on to find out.
-
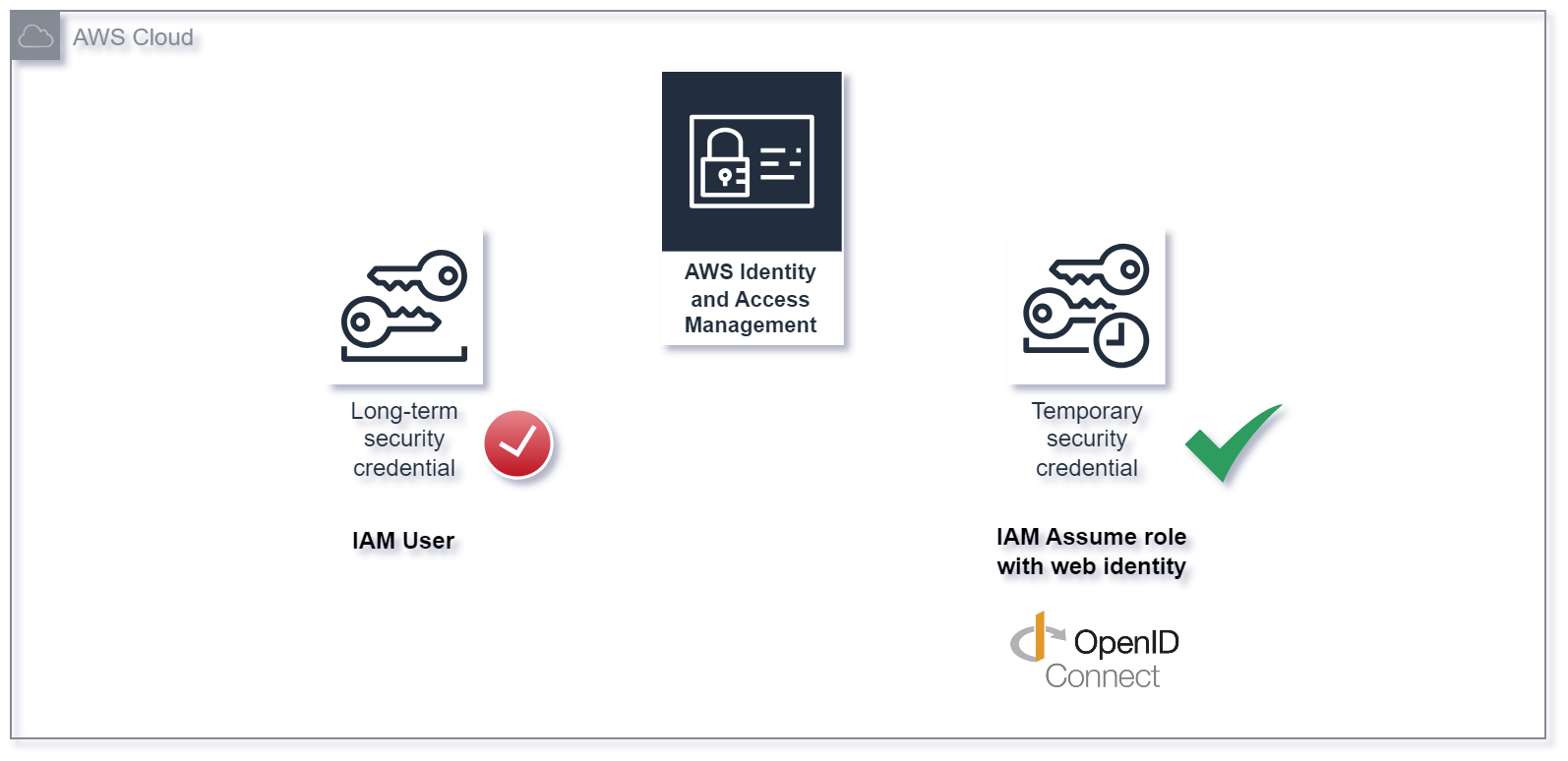
Adopt Open ID Connect (OIDC) in Terraform for secure multi-account CI/CD to AWS
In this post we will explore how we can increase our security posture by leveraging Open ID Connect (OIDC) as authentication mechanism in CI/CD pipelines for deploying Terraform based infrastructure to Amazon Web Services (AWS). The first design principle of the Security Pillar of the AWS Well-Architected Framework sounds as follows:“Implement a strong identity foundation:…
-

Achievement unlocked: AWS Black Belt Pilot – Containers
In my position as Principal Cloud Architect in Sopra Steria, I am fortunate to be involved in exciting projects where I get the opportunity to continuously expand my knowledge and expertise. Sopra Steria is an AWS Partner and recently I have been working on a project where Amazon Web Services invited a group of architects…
-
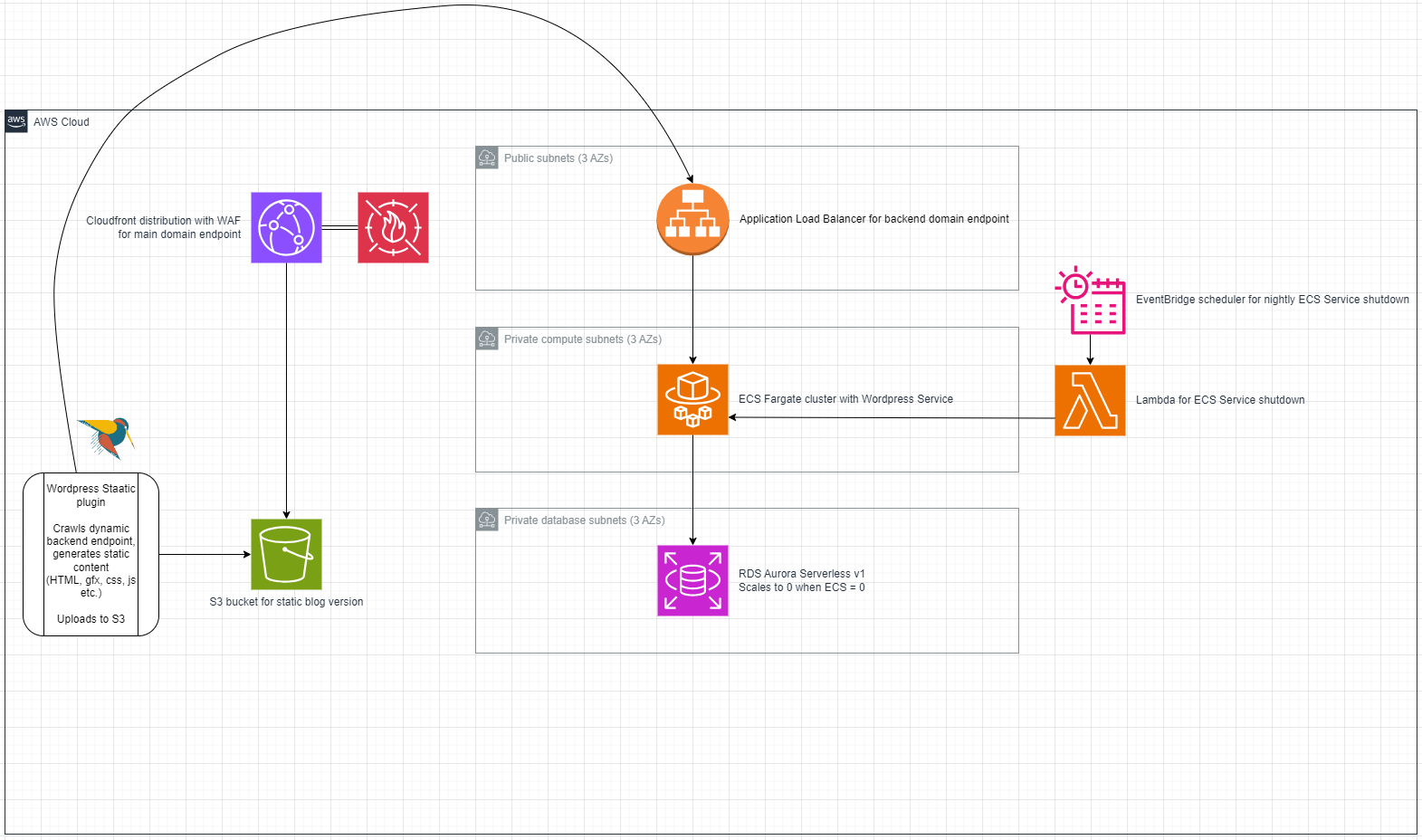
Deploying WordPress on ECS with AWS Copilot
When I decided to start a blog I naturally went through a lot of thoughts regarding how to solve my desired outcome. My main goal is to share knowledge and things I’ve learned which might be useful for others, but also to learn something new for myself during the process. I quickly decided that I…
-
Hello world!
Citizens celebrate, my blog is up and running. Stay tuned for personal reflections, experiences, cloud technology and Amazon Web Services.